This Linux Distro Is Focused on Maximum Privacy and Anonymity, Here’s How to Use It
Protect your privacy with Tails.
Quick Links
- Privacy and Anonymity Online
- What Tails Can Do for You
- Tails Can’t Save You From Yourself
- Booting Into Tails
- Using Tails
- Tails You Win
Key Takeaways
- Free online services track your usage and use your data for their profit without you knowing.
- Tails, a Linux-based operating system, is designed for one thing: to provide privacy and anonymity online.
- While Tails is effective, user error can expose you, necessitating caution and awareness.
Is online privacy a lost cause? Tails Linux lets you be private online, just as long as you understand its limitations, use it within those limits, and don’t inadvertently blow your cover.
Privacy and Anonymity Online
The phrase “If it’s free, you’re the product” has been around in one paraphrased form or another since 1973, when it was first leveled at commercial television. The words could have been tailor-made for the internet.
When you use a free online service that’s provided or backed by a commercial entity, you’re paying to use that “free” service by permitting them to collect, process, and share data about your online activities and anything else they can deduce about you.
Typically, this leads to personalized advertising, but your data could be used for altogether more shady purposes. One infamous example is the Cambridge Analytica scandal, which saw the personal data of multiple millions of Facebook users harvested and used in 2016 in an attempt to benefit two presidential candidates.
If you live in an oppressive regime, the use of forbidden or banned services and websites can even lead to imprisonment, so privacy and anonymity are paramount.
Whether you use Linux, macOS, Windows, or anything else, trying to access the internet or the web without being digitally spotted and tracked is almost impossible.
What Tails Can Do for You
Tails OS, known simply as Tails, directly addresses this problem. It’s a Debian-based Linux distro born out of the merger of two earlier privacy projects, Amnesia and Incognito. Tails stands for “The Amnesiac Incognito Live System.”
It is designed to record nothing and to leak as little information as possible. Tails runs in RAM and writes nothing to the hard drive. When you shut it down, it overwrites the RAM it used so that nothing can be extracted from your computer’s memory. That’s what the amnesiac part of its name refers to.
As for the incognito part, Tails forces all external network connections through the Tor network. Tails blocks any connection requests that try to side-step Tor and connect directly to the internet.
The Tor network is a volunteer-run network of nodes. It encrypts and routes your connection into, through, and back out of the Tor network. Your connection will be routed through at least three nodes.
Unlike regular internet traffic, your data packets are only labeled with where they need to go. Normal data packets carry the details of their origin with them, too. Because Tor data packets don’t carry details of where they come from, it’s practically impossible for someone to backtrack down through your connection to identify you.
Tails is best used as a live distribution, booted from a USB flash drive. There are no changes made to the computer you plug the USB drive into, and nothing is written to the USB drive unless you specifically set up some persistent storage. Everything in the persistent storage is automatically encrypted.
Tails Can’t Save You From Yourself
Tails OS is as great as it sounds, but it isn’t foolproof. There’s the human element to consider. It’s still possible for you to do something that side-steps Tails’ best efforts to grant you privacy and anonymity.
Remember that there has to be a connection between the last Tor node your traffic passes through, and the service or website that you’re connecting to. That last link has to be made over the plain old, regular internet.
That means your traffic could be at risk of capture and analysis. One way to make that more difficult is to only connect to sites or services that use encrypted connections, such as HTTPS-enabled websites.
Even then, only use a single Tails session to conduct a single activity. To prevent anyone from determining that two of your activities were performed by the same person, reboot Tails and get a fresh session for each successive action you wish to perform.
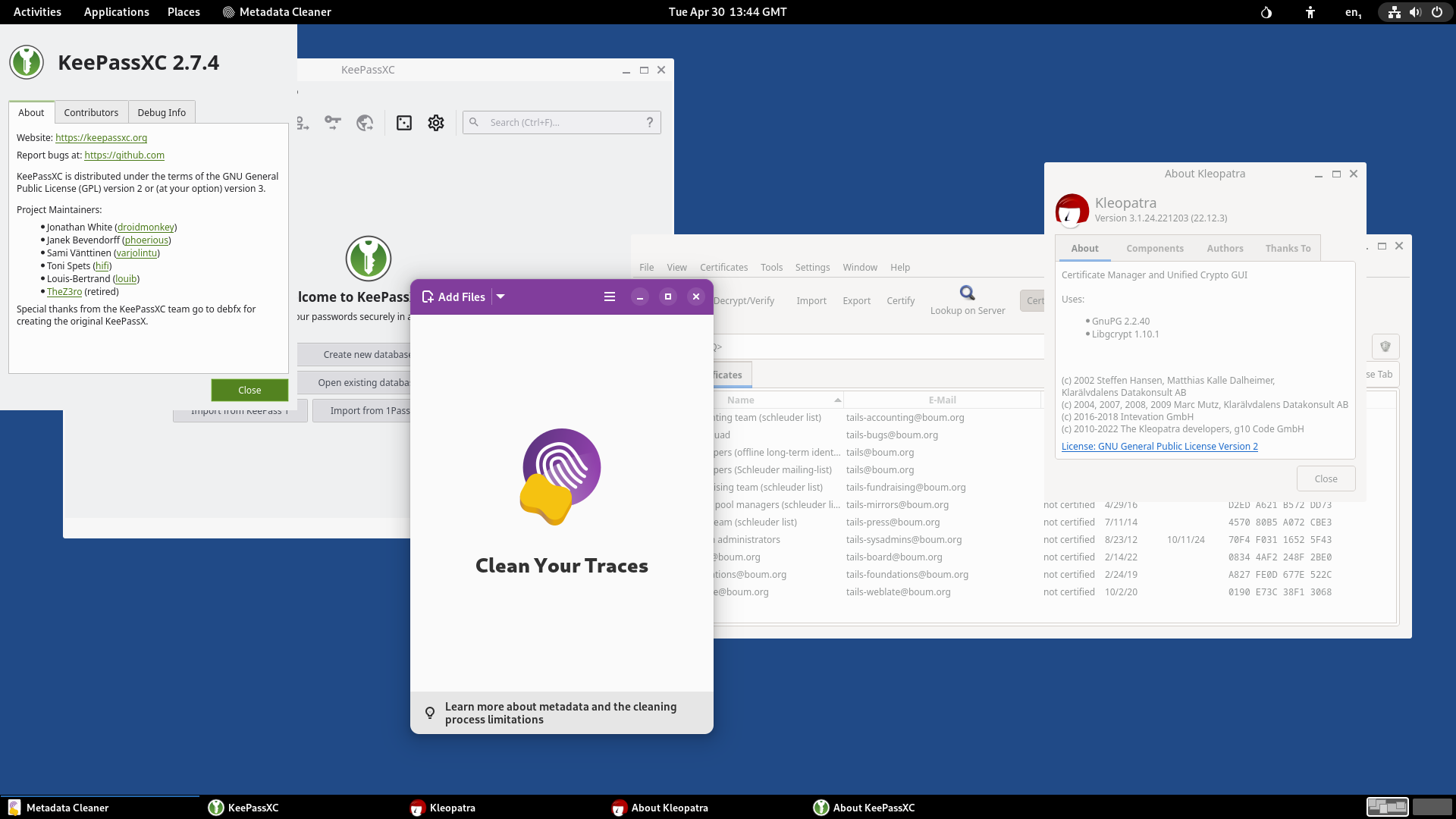
If you’re going to transfer files or images, clean the metadata from them first. Tails includes a metadata cleaner tool for this purpose.
Storing information on your USB drive, even though it’s in your persistent encrypted storage, is risky. If your USB drive falls into the wrong hands, the attackers have something in their possession they can make repeated cracking attempts on.
And remember, your ISP can tell you’ve used the Tor network, even if it doesn’t know what you did while you were connected. They won’t know what you did, but they’ll know you used Tor to do it.
Booting Into Tails
To use Tails, download an image and follow the easy steps to burn it to your USB drive. All data is erased from the drive, so make sure you have nothing of importance on it before you start.
With Tails installed on your USB drive, plug it into a computer, and reboot it or power it on. During the boot process, hit the keystroke(s) that opens up your Boot Menu. You might need to press a key such as F12 or Esc at a particular moment during the computer’s boot process.
Computers usually display a message telling you the key you need to press, and when to press it. These messages are usually fleeting, so you might need to boot the computer twice. Once to read the message, and once more to hit the key.
If your computer doesn’t give you a message at all, you can discover the key press by searching online for the make and model of your computer.
In your boot menu, select your USB drive as the boot device, and let the boot process continue. Your computer will boot up into Tails.
Using Tails
Tails boots into a welcome screen that allows you to set your keyboard layout. You can also set a passphrase that’s used to secure your persistent storage, if you’re going to use it.
You can change your keyboard layouts later using the usual GNOME Settings application. There’s a separate Persistent Storage management application as well.
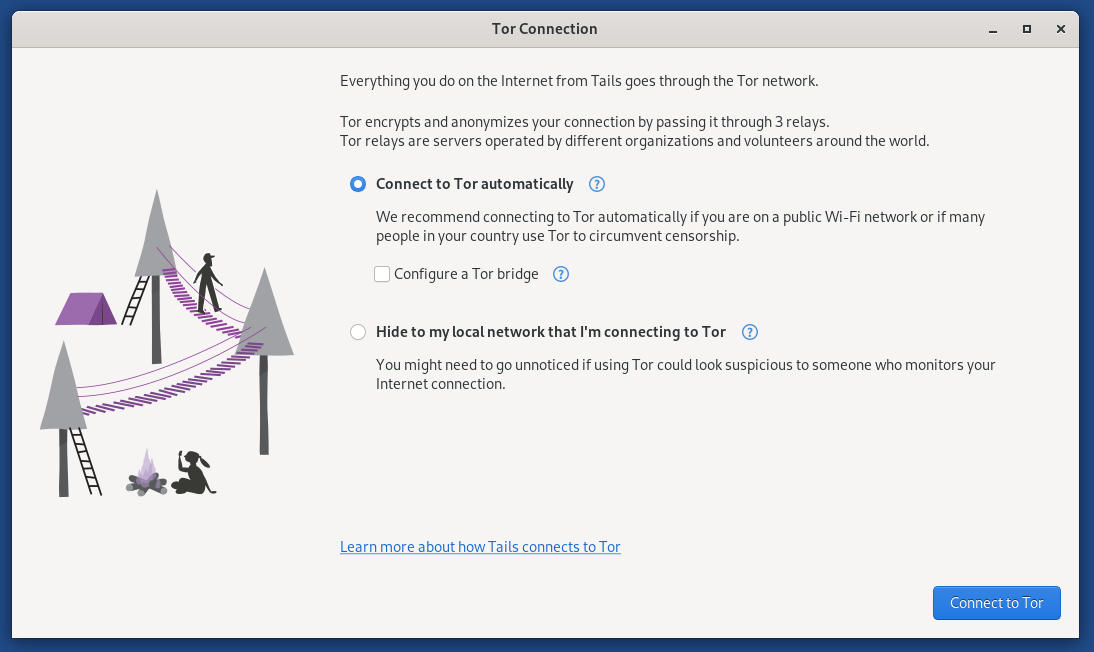
The first thing Tails offers to do is to connect to the Tor network automatically.
Click the “Connect to Tor Automatically” radio button and click the blue “Connect to Tor” button.
In a moment, you’ll see the successful connection message, and the onion icon in the system area of the top bar no longer has a cross over it.
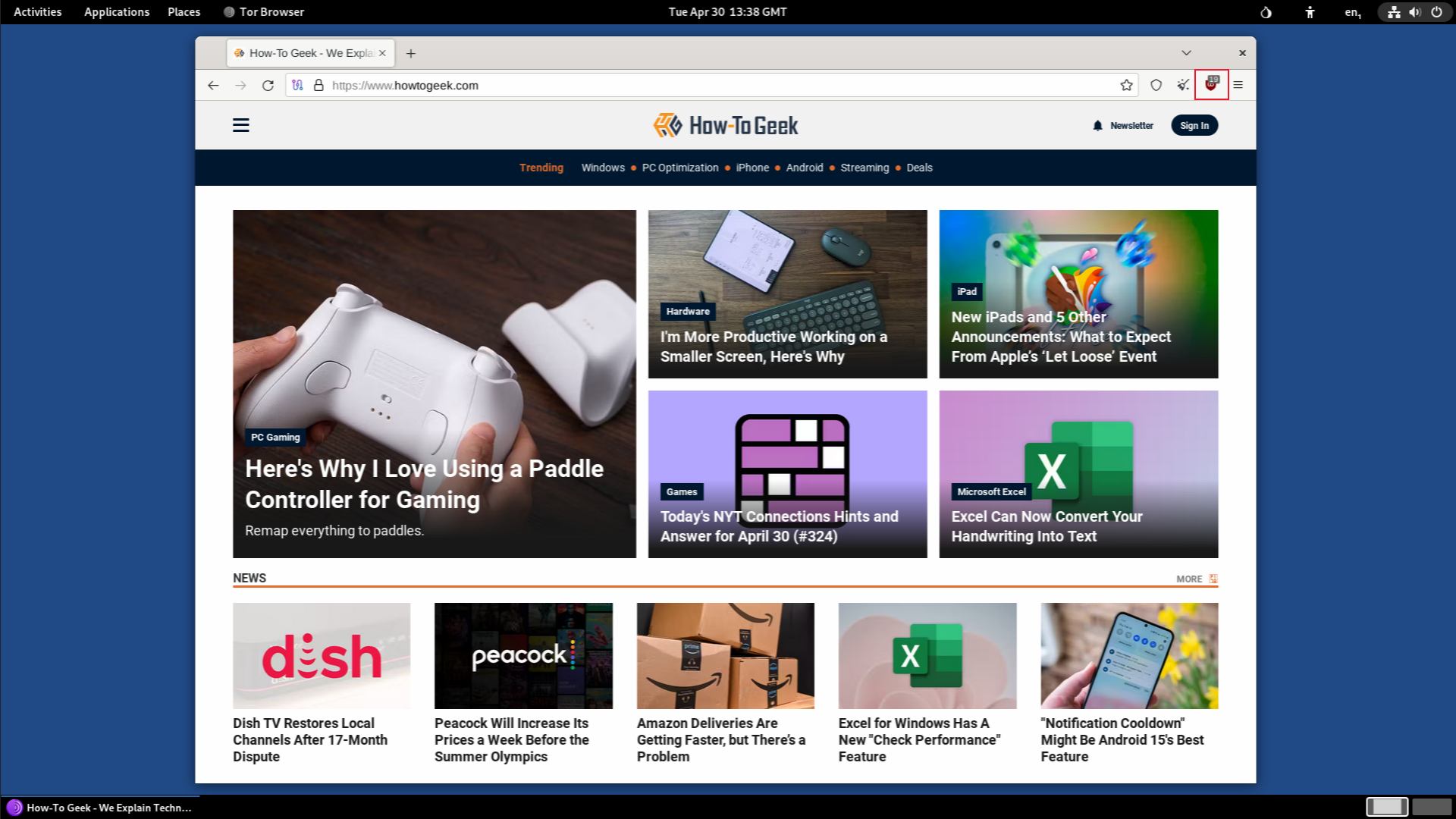
Clicking the Activities icon in the top left of the top bar displays the dock, which is populated by commonly used programs, such as the Tor browser.
Launching the Tor browser gives you a secure web browser. The uBlock Origin content filter and ad blocker extension is installed by default.
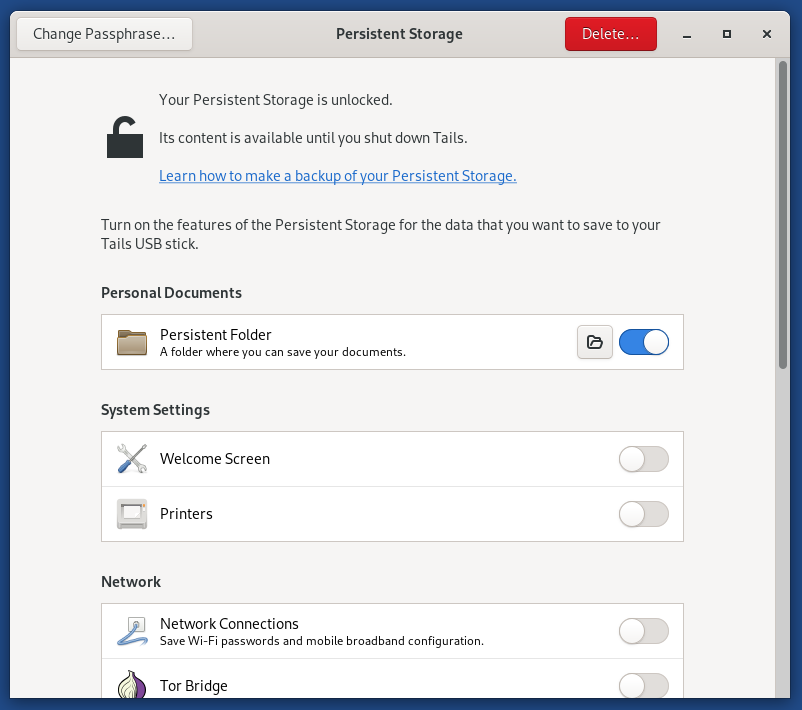
You also find Persistent Storage in the dock. This is an application that lets you manage your persistent storage. If you have persistent storage turned on, some system settings and configs can be saved and used the next time Tails is launched.
Because Tails doesn’t save anything you do, if you install additional software, it’s actually re-installed each time Tails boots, using the installation files in your persistent storage.
Tails provides other security applications, such as KeePassXC for password storage, a metadata wiper, and Kleopatra, an application that automates the handling of security certificates.
Tails You Win
Tails is not intended to be your daily driver operating system, it’s too slow and too purposely restricted. However, Tails is the most popular operating system of its type, and with good reason. It is constructed from the ground up with privacy and anonymity in mind. And it can deliver that, as long as you use it with awareness.
It’s like a cloak of invisibility. On the face of it, it’s fantastic. But you need to make sure it’s pulled down to the ground so your feet don’t show.