The Latest Smartphones Still Can’t Address This Hidden Security Concern
Cybersecurity
Key Takeaways
- Improper credentials usage by application developers is the top mobile security risk in 2024.
- Verify that the apps you use are storing and handling password data appropriately.
- Avoid insecure apps by checking password policy, error messages, encryption, and permissions.
Smartphones are becoming better every year, not just in terms of form factor and usefulness but also in the strength of their security features. However, phone manufacturers still cannot fully eliminate security risks that come from improper credentials usage on the part of application developers.
Your Phone Can’t Protect You From a Developer’s Improper Credentials Usage
According to the OWASP Mobile Top 10, improper credential usage constitutes the most significant mobile security risk in 2024. Application credentials include passwords and other sensitive information you use to access an app’s features or services. It is, unfortunately, common for developers to mishandle these types of credentials for the sake of their own convenience.
An example of improper credential usage includes hardcoding passwords into the app’s source code so that they are easier to find and reference for future processes. As a result of this, though, malicious parties gain access to crucial passwords if they manage to breach their way to the source code itself.
Developers should use secure means of transmitting and storing sensitive data, leveraging a high level of encryption. Weak application security is another example of negligence when it comes to handling user credentials. Insecure processes will make your passwords that much more vulnerable.
This lack of application security happens on the developer side. While many app stores have measures in place to test for security vulnerabilities before listing an app, some threats do slip through the cracks. Your phone itself cannot protect you when this happens, even if you have the latest security updates.
How to Know if an App is Using Your Credentials Properly
Your personal information is on the line when developers are guilty of improper credentials usage. Ideally, you should never have to worry about security risks when you use a trusted app marketplace like Google Play and its alternatives. Still, it is never a bad idea to do your due diligence to verify safety.
The first and easiest way to check if an app will use your credentials properly is to review its password policy. If an app does not require you to create a particularly strong password, for example, they might be cutting other corners in terms of security as well. You should also be wary of an app’s error-handling practices by considering the error messages displayed upon a failed login – a detailed error message such as “Username does not exist” is actually a poor security practice, as this can help malicious parties narrow down the list of accounts they might try to exploit.
If you are already using an application and have reason to suspect it might be mishandling your credentials, there are in-depth steps you can take to see how the software is using your data. Scan the outgoing data packets with software like Wireshark to see if the app is encrypting your password. If a lack of encryption becomes apparent, this is a huge red flag for the safety of your personal information.
How to Avoid Insecure Applications in the First Place
The most important rule of thumb to follow is to only download applications or software from trusted sources. Even when using a personal device, follow the same tips for professional IT cybersecurity. Major app stores have security testing and scanning measures that make it much more unlikely for vulnerable apps to reach you. Random websites and suspicious links do not have any such guarantees.
Even if you’re using a marketplace like Google Play, though, you should still check an app’s reviews before installing. Check for user comments that indicate poor security. Don’t hesitate to go the extra mile in researching a developer more deeply as well. You can never be too cautious in ensuring that the files you download come from a reputable place.
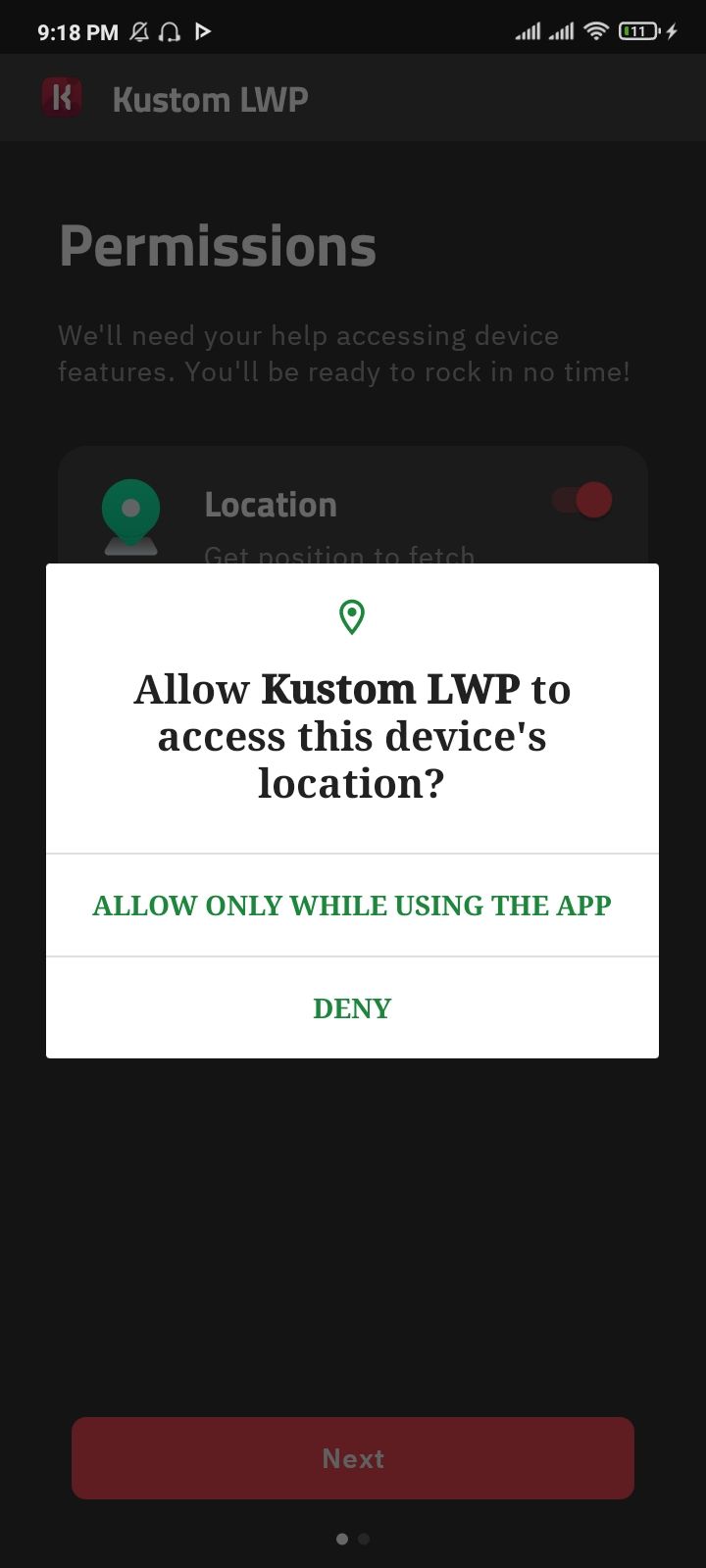
Last but not least, don’t forget to check what permissions the app requests from you when you first install it. Many apps will ask to access your photos, location data, or other information. Ask yourself if the app truly needs the requested permissions to fulfill its purpose. Most importantly, do not grant any additional permissions unless you are completely sure that the app, its developers, and the place you downloaded from are all absolutely trustworthy.
Your smartphone does so much more for your digital security than you likely realize. Even so, there will always be limitations to how much protection the hardware itself can offer. Do what you can to improve your own cybersecurity and you will be much safer in a landscape dominated by tech-savvy ne’er-do-wells.