Cybersecurity researchers at Cado Security have identified a new malware-as-a-service (MaaS) targeting macOS users and cryptocurrency holders.
The new macOS malware dubbed “Cthulhu Stealer” was first spotted in late 2023 and is being sold as a service on the dark web for $500 per month.
This malicious malware’s main functionality is to extract sensitive information from infected Macs, such as browser cookies, system passwords, saved passwords from iCloud Keychain, cryptocurrency wallets from various stores, including game accounts, web browser information, and even Telegram Tdata account information.
Cthulhu Stealer is an Apple disk image (DMG) bundled with two binaries designed for x86_64 and ARM architectures. It is written in GoLang and disguises itself as legitimate software, imitating popular applications such as CleanMyMac, Grand Theft Auto VI, and Adobe GenP, wrote Cato Security researcher Tara Gould in a recent Cado Security report.
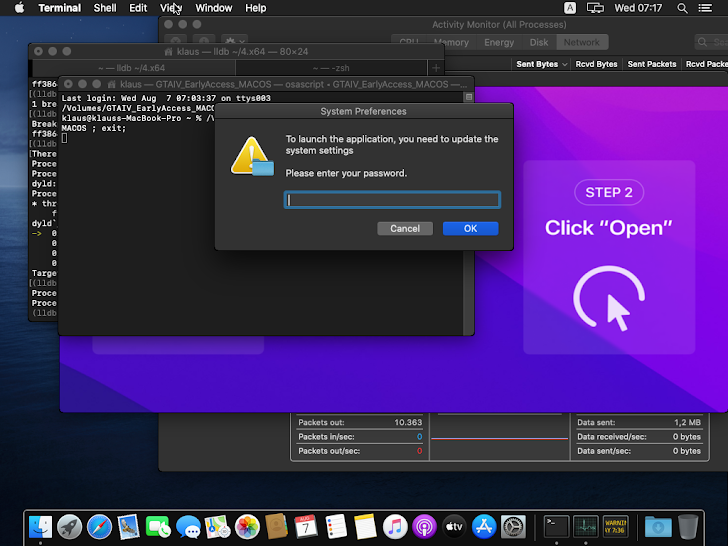
Once the user mounts the dmg file, the user is asked to open the software. After the file, osascript, is opened, the user is prompted to enter their system password through macOS’s command-line tool, which runs AppleScript and JavaScript.
After entering the initial password, a second prompt requests the user’s MetaMask password. It then creates a directory in ‘/Users/Shared/NW’ to store stolen credentials in text files.
The malware is also designed to dump iCloud Keychain passwords in Keychain.txt using an open-source tool called Chainbreak. The stolen data is compressed and stored in a ZIP archive file, after which it is exfiltrated to a command-and-control (C2) server controlled by the attackers.
Once the Cthulhu Stealer malware gains access, it creates a directory in ‘/Users/Shared/NW’ with the stolen credentials stored in text files. It then proceeds to fingerprint the victim’s system, collecting information including the IP address, system name, operating system version, hardware, and software information.
“The functionality and features of Cthulhu Stealer are very similar to Atomic Stealer, indicating the developer of Cthulhu Stealer probably took Atomic Stealer and modified the code. The use of osascript to prompt the user for their password is similar in Atomic Stealer and Cthulhu, even including the same spelling mistakes,” added the report.
However, reports indicate that the threat actors behind the Cthulhu Stealer may have ceased operations, reportedly due to payment disputes and accusations of being scammers or participating in an exit scam. This led to a permanent ban from the marketplace where the malware was promoted.
Although macOS has long been considered a secure system, malware targeting Mac users remains an increasing security concern. To protect from potential cyber threats, users are advised always to download software from trusted sources, enable macOS’s built-in security features such as Gatekeeper, keep the system and apps up to date with the latest security patches, and consider using reputable antivirus software to provide an extra layer of protection.
“Hey there! Just so you know, we’re an Amazon affiliate. This means if you buy something through our links, we may earn a small commission. It doesn’t cost you extra and helps keep our lights on. Thanks for supporting us!”