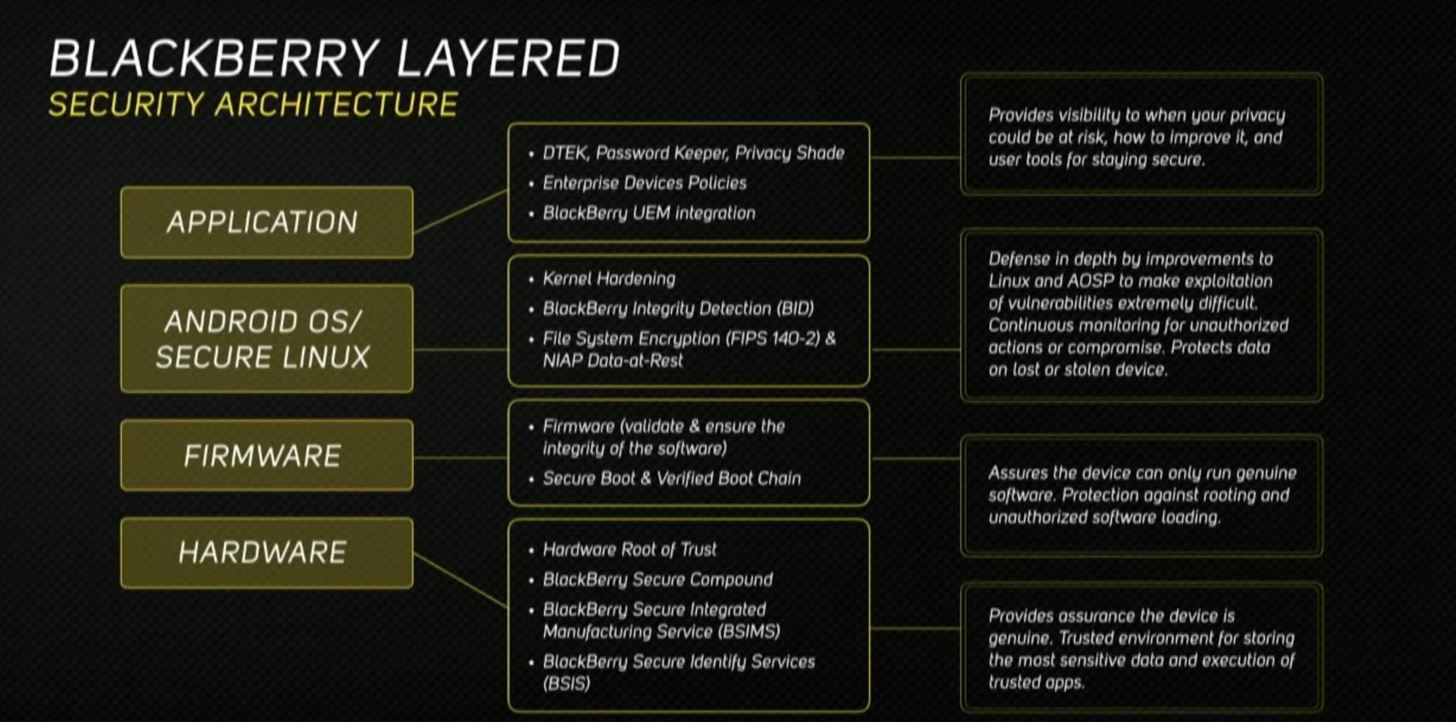
We need to take our privacy and security much more seriously. Whether it’s malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.
Once again, a BlackBerry device topped our list of the best phones for privacy and security. BlackBerry, which has always been known for their protection, brought many of the security enhancements from their old OS (BB10) to Android when they made the switch. The result is the most secure Android smartphone on the market, and the best option for privacy-conscious individuals.
1. Hardware Root of Trust & Secure Boot
Protection for the BlackBerry KEY2 starts during manufacturing when each device’s processor is injected with cryptographic keys. These keys are unique to every individual handset off the line, and are vital during the Secure Boot Process.
When you turn on your phone, even before you are presented with your lock screen, each component of the hardware and software is checked for any tampering. If any component fails the test, the KEY2 will not boot. This makes it infinitely harder for hackers or law enforcement to bypass BlackBerry’s other security measures.
2. Rollback Protection
One strategy used by thieves and hackers is to downgrade your phone to an older version of Android in an effort to exploit older vulnerabilities not addressed in the previous version of Android. However, the KEY2 protects against this by preventing any older version of the OS from being installed — in other words, “Rollback Protection.”
3. Kernel Hardening
At the heart of every Android operating system version is the Linux kernel. The kernel is an essential component of Android, making it a high target for hackers. While Android does a great job patching any vulnerabilities in the kernel, BlackBerry takes it further.
BlackBerry altered the kernel of the KEY2 to remove any unnecessary functionality. BlackBerry also reviewed previous exploits that plagued other Android devices and patches the KEY2 before it leaves the factory. And, while most Android devices receive monthly security patches sent out by Gooogle, the KEY2 will receive additional patches whenever BlackBerry catches a vulnerability that endangers the integrity of the kernel.
4. Unrootable
As of the time of this writing, no Android-powered BlackBerry smartphone has ever been rooted. It’s BlackBerry’s goal to keep it this way. While rooting does open the door for additional features, it leaves your device in a compromised state. Without the capability of rooting, the KEY2 can avoid exploits which depend on root to compromise the security of your device.
5. DTEK & BlackBerry Integrity Detection
DTEK is the KEY2’s central hub for all things security related. On the main page, you’ll find a gauge which visual displays how secure your device is, along with a list of any factors preventing maximum security.
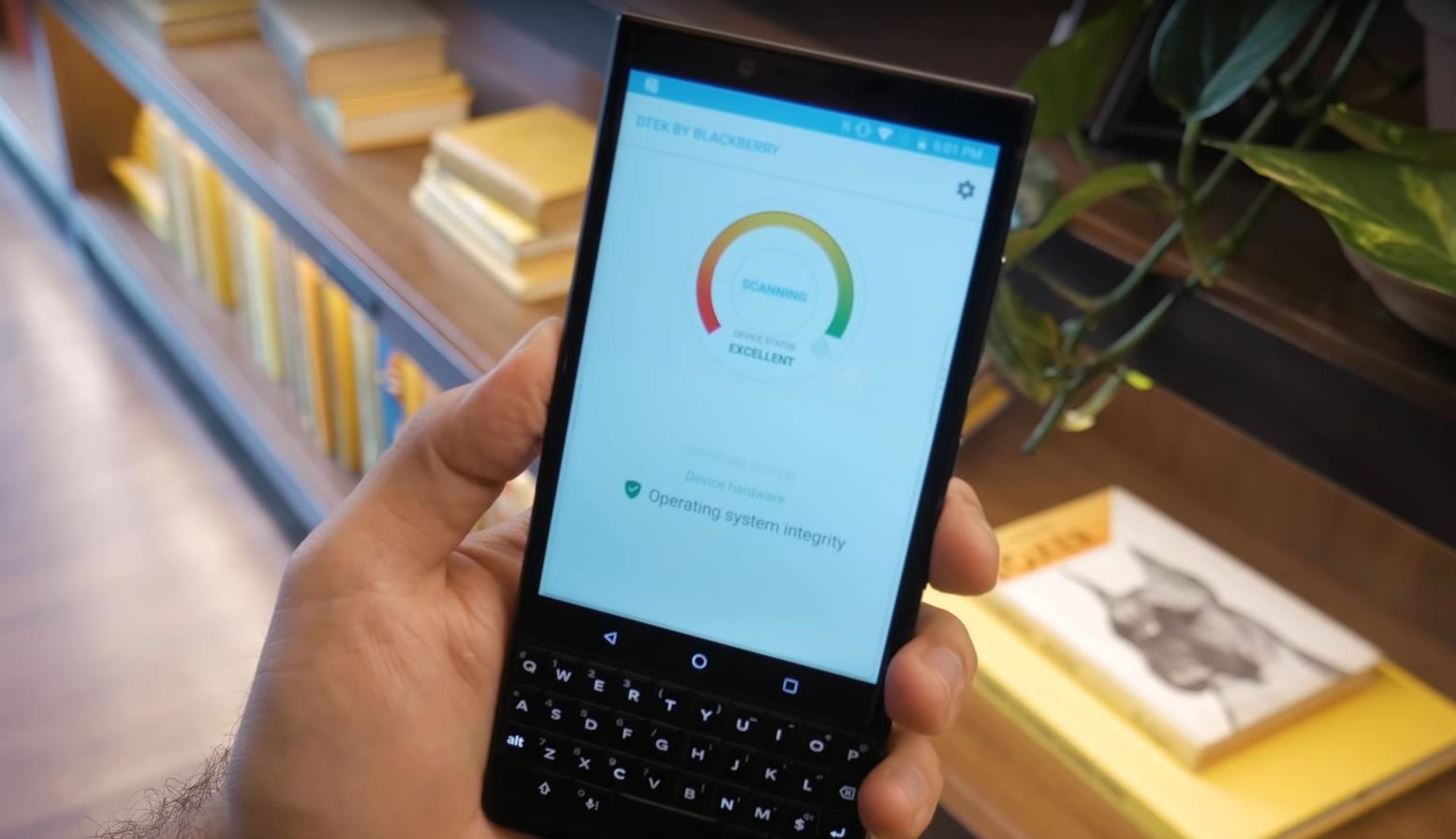
DTEK automatically monitors the operating system and apps, looking for any signs of potential threats to your defenses. DTEK also leverages the BlackBerry Integrity Detection (BID) to alert you of threats in real-time.
BID is a system of triggers placed all around your device that monitors any changes to major components. Once this occurs, DTEK will warn you and provide options you can take to stop any further compromise. Additionally, you can set up your own triggers for sensors, such as an alert anytime an app asks to use the camera in the background.
6. Full-Disk Encryption
Unlike other Android Phones running Android 7.0 Nougat or higher, the KEY2 encrypts it hard drive using full-disk encryption rather than file-based encryption. With full-disk encryption, to access any file on the phone’s storage, you need to know the device password. The password is used to create a key, which the KEY2 stores in the BlackBerry Secure Compound, a trusted execution environment (TEE).
Furthermore, their full-disk encryption is compliant with the US government’s computer security standard, FIPS 140-2. Not only does them allow to fulfill the requirements needed to keep one of their biggest customers, but it also provides you access to security that is secure enough for the US government.
7. Privacy Shade
Seeing how we often use our phones in public, BlackBerry included an app which protects us from nosey neighbors. Using either the Quick Setting toggle or the default three finger swipe down gesture, you can launch Privacy Shade to darken your display except for one small area, allowing you to continue to view your screen safely. Privacy Shade lets you control how dark you make the screen as well as the size and shape of the visible area.
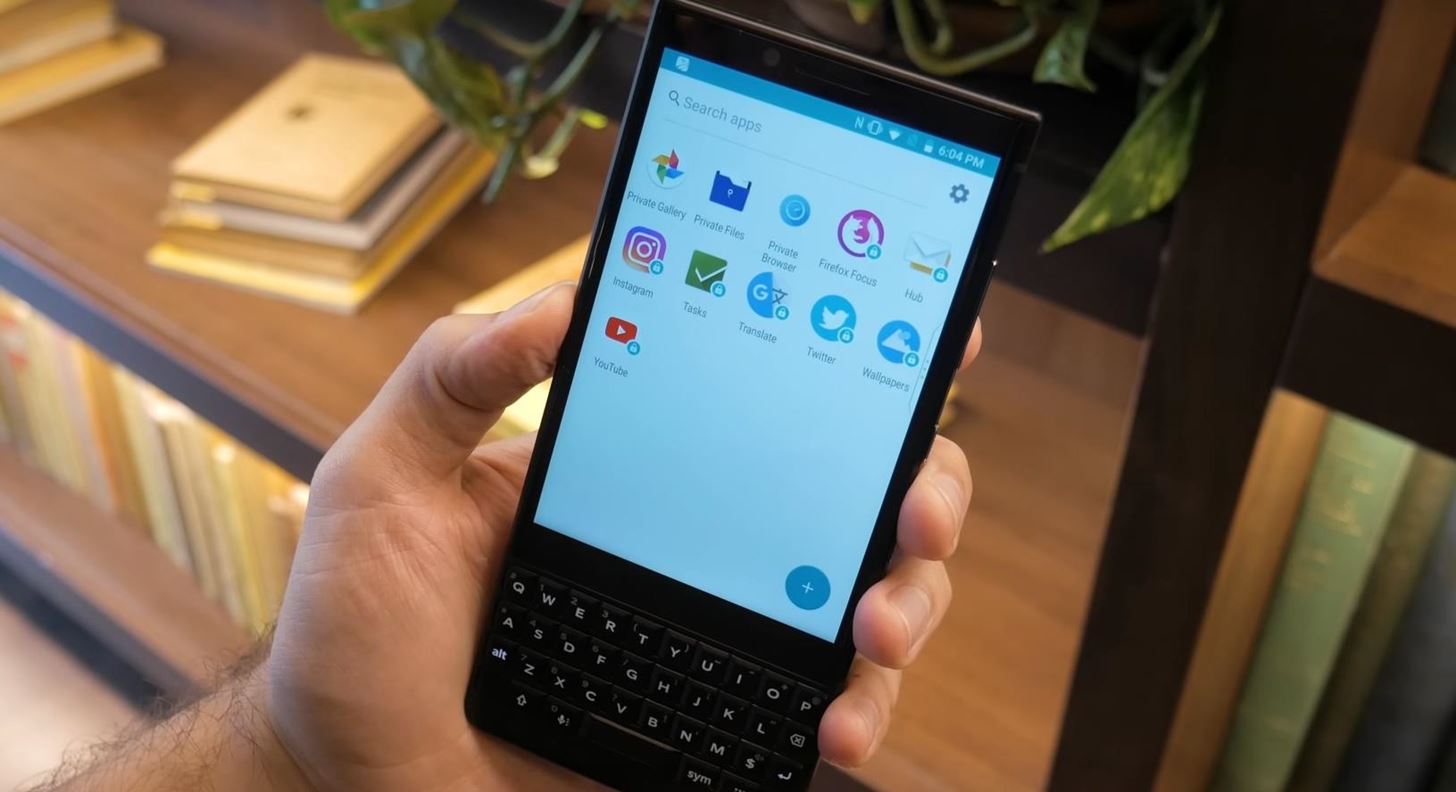
8. Locker
BlackBerry understands that sometimes we need to lend our phones to others. Whether it’s a friend needing to make a call or a significant other who doesn’t trust us, sometimes our unlocked phone will be in the hands of others. To protect our data in those situations, BlackBerry included Locker.
Locker is a secure folder that requires fingerprint or password authentication to access. This folder can store both apps and files that won’t appear in the app drawer or file manager. These apps and files are exempted from cloud backups as well.
Locker also includes a browser, Firefox Focus, to view the web privately without worrying about someone checking your browsing history. Additionally, Locker is also integrated into the camera. When taking a photo, a light tap of the space bar will automatically save the image in the Locker instead of the public gallery.
With the KEY2, BlackBerry took a strategic approach as to how they will protect your privacy and keep your phone secure. The enhancements and tools added improve the Android operating system powering it and allow the KEY2 to separate itself from the competition.
We all need to take privacy and security more seriously. Often, we don’t pay attention until something happens, and only then do we realize the severity of the impact. With the KEY2, BlackBerry does the bulk of the work, allowing the more essential components to run automatically. What are your thoughts on the KEY2? Let us know in the comment section below.
Hot Deal: Set up a secure second phone number and keep your real contact details hidden with a yearly subscription to Hushed Private Phone Line for Android/iOS, 83%–91% off. It’s a perfect second-line solution for making calls and sending texts related to work, dating, Craigslist sales, and other scenarios where you wouldn’t want to give out your primary phone number.
“Hey there, just a heads-up: We’re part of the Amazon affiliate program, so when you buy through links on our site, we may earn a small commission. But don’t worry, it doesn’t cost you anything extra and helps us keep the lights on. Thanks for your support!”










